In the current digital landscape, the increasing rise of cybersecurity threats has emphasized the importance of cyber forensics. As institutions face a variety of challenges related to data leaks, malicious software infections, and other cyber incidents, comprehending the nuances of digital investigations has never been more crucial. This article explores real-world cases that reveal key insights and lessons learned from actual cyber forensics investigations. These real-life case studies not only illustrate the effectiveness of forensic tools but also provide a deeper understanding of the procedures involved in emergency file recovery and incident response.
As we explore these case studies, we will provide applicable guidance and strategies that can be employed in data recovery efforts. The insights gleaned from these studies are invaluable for professionals in cybersecurity, information technology teams, and individuals interested in enhancing their knowledge of digital forensics. By examining safeguard your information and difficulties faced during these investigations, audiences will gain insights into best practices for protecting data and reacting to digital threats. Whether you are a seasoned expert or beginner to the field, the insights shared here will arm you with crucial information to navigate the complex world of cyber forensics.
Electronic forensics is the method of revealing and analyzing electronic data to examine crimes and security incidents. It serves a crucial role in the field of cybersecurity, assisting organizations in recovering lost data and understanding the occurrences leading up to a breach. This field includes the acquisition, preservation, and analysis of digital evidence from diverse devices, ensuring that the information is dependable and can be used in legal proceedings if needed.
In the field of cyber forensics, several crucial tools and methodologies are used. Computer forensics tools enable investigators to extract and analyze data from hard drives, mobile devices, and networks. These tools not just help in recovering deleted files but furthermore in identifying the methods used by offenders to compromise systems. The integration of forensic methods with incident response strategies is crucial for effectively managing cybersecurity threats.
Furthermore, comprehending digital forensics is not limited to technical aspects; it additionally encompasses legal and ethical considerations. Investigators must be prepared to adhere to strict protocols to safeguard the integrity of the evidence gathered. By adhering to these guidelines, they can ensure that the findings are valid in court and that the rights of individuals are respected throughout the investigation process. This multifaceted approach is what makes digital forensics a vital element of modern cybersecurity strategy.
Data recovery is a vital aspect of cyber forensics, especially when dealing with situations where data has been lost or erased. One typical technique involves employing specific software tools designed for emergency file recovery. Such tools can scan storage devices for remnants of erased files, allowing forensic professionals to retrieve valuable data that may not be accessible through conventional file browsing methods. Their efficacy depends with the state of the device, but they are essential for retrieving critical evidence in many cases.
An additional technique focuses on the physical recovery of information from defective hardware. When machines suffer from physical failures, such as hard drive crashes or water damage, forensic experts may use advanced methods to extract information directly from the device. This typically requires the use of sterile environments and precise equipment to reduce the risk of further loss. Techniques like platter swapping and circuit board repairs enable experts to retrieve information in cases where standard software recovery methods fail.
In addition to these methods, digital forensics also includes analyzing network data to recover data lost during security incidents. By capturing live traffic and examining logs, forensic investigators can uncover traces of deleted files or identify unauthorized access attempts. This approach not only aids in recovering information but also helps in understanding the situation and implications of the incident, providing deeper insights into the security vulnerabilities that may have contributed to the information loss in the first place.
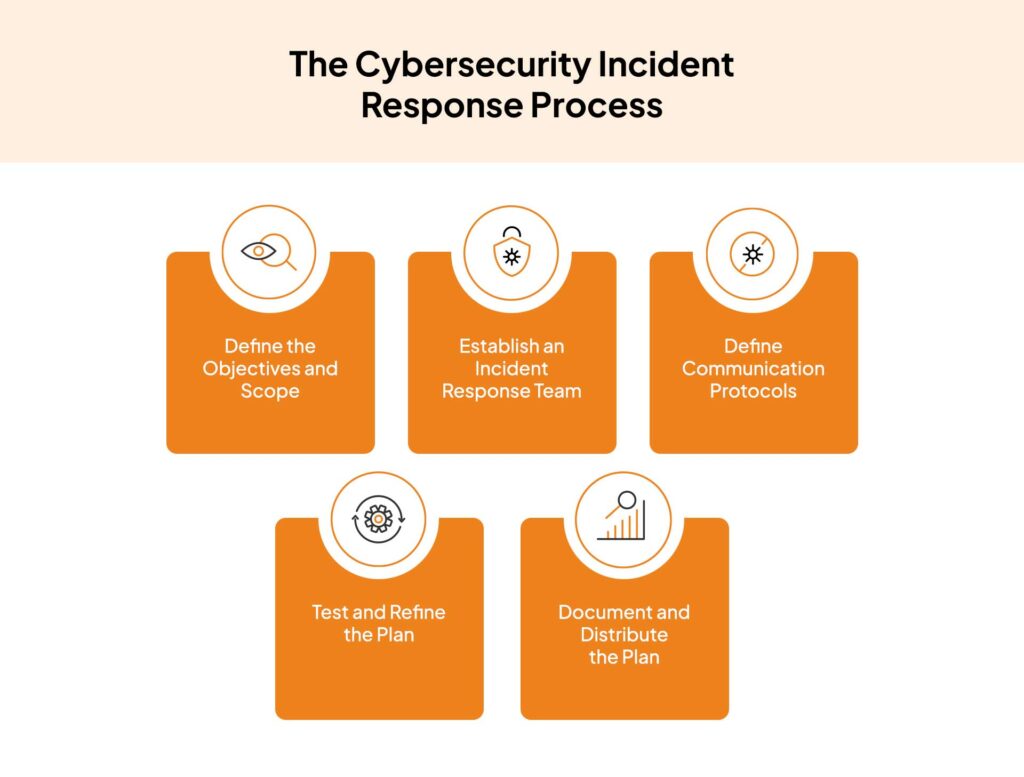
An impactful cybersecurity incident plan is crucial for organizations to minimize damage during a cyber assault. This method typically involves a clearly outlined framework that specifies duties and responsibilities, information guidelines, and incident classification. By having a thorough strategy in place, entities can respond swiftly to crises, which is critical in mitigating the impact of a security incident. This readiness reduces the chance of data compromise and enhances general resilience against future risks.
Incident reaction should also include consistent education and simulations for the response team. Participating in tabletop exercises helps teams practice their skills in real-world situations, ensuring that all members understand the protocols and can respond together when an incident happens. Additionally, utilizing digital investigation tools during these exercises can enable groups to better grasp the techniques for tracking, examining, and restoring compromised information. Ongoing education and readiness strengthen an organization's readiness to handle real events swiftly and effectively.
Furthermore, after addressing to a cybersecurity incident, organizations should carry out a thorough analysis to identify vulnerabilities and enhance their defenses. This post-incident review helps in updating the information restoration guide and refining emergency data restoration processes, ensuring that insights learned inform upcoming plans. By regularly adapting incident plans based on real-life situations, companies can enhance their security standing and reduce the likelihood of recurring events.